Originally posted here [Old Blog]: http://witcoat.blogspot.com/2017/06/xss-on-bugcrowd-and-so-many-other.html
Hi all,
This is my first Blog post. I recently found Reflected Cross Site Scripting(XSS) vulnerability on Bugcrowd main domain which had huge impact.
Secret Parameter:
This didn’t only work on 404 page but also on the homepage for ex: https://bugcrowd.com?locale=xss. However this parameter didn’t seem to do anything else, so I immediately reported to Bugcrowd. When I woke up in the morning, I came to know that this bug was rather in Locomotive CMS, bugcrowd worked around showing that page at router level to mitigate the impact .
Knowing this I immediately checked out Locomotive CMS and so was their website vulnerable.
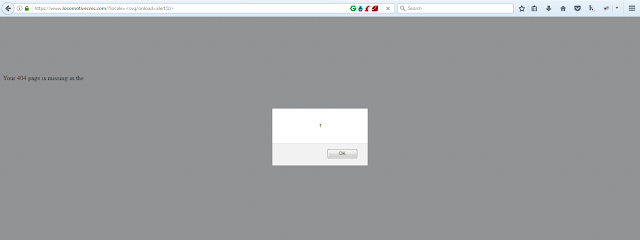
If your application is using Locomotive CMS, chances are you are also vulnerable, but don’t worry If you find that you have this vulnerability, I believe there is a patch out there. Contact Locomotive CMS for more information.This had huge impact as all the submission data and other important information is hosted on main domain which means one click and few seconds of javascript processing will steal all the data from the user and take actions on behalf of users(CSRF).
After few days Locomotive fixed the bug and allowed disclosure. You can easily find some locomotive CMS application to test this out.Bugcrowd rewarded $600 for this, I didn’t agree with the reward amount but it was really nice to see the Quick Fix.